Sotware Supply Chain
Secure every component of the software development lifecycle
Federal Guidelines Have Changed. Has Your Software Security?
With threat actors targeting open-source artifacts, software development systems, and DevOps pipelines, it’s impossible to exaggerate just how risky the software supply chain is today. With so many moving components to the software lifecycle, threats can enter at multiple phases. Even if you apply the best security practices in developing your own code, applications, and infrastructure, you still depend on third-party components completely outside of your control.
The Cybersecurity Executive Order (EO) 14028 addresses cyber risks in the software supply chain and sets the stage to establish baseline security standards for developing software—especially critical software—that is sold to the federal government. Key provisions include requiring developers to have greater visibility into their software and making security data publicly available. But that’s just the start.
The ever-growing complexity of software, infrastructure, and dependencies combined with the growing number of pervasive and increasingly malicious attacks targeting the supply chain make defending against such attacks not only a priority but a necessity. Merlin offers innovative, disruptive solutions engineered to strengthen agencies’ ability to prevent, detect, mitigate, and respond to supply chain attacks.
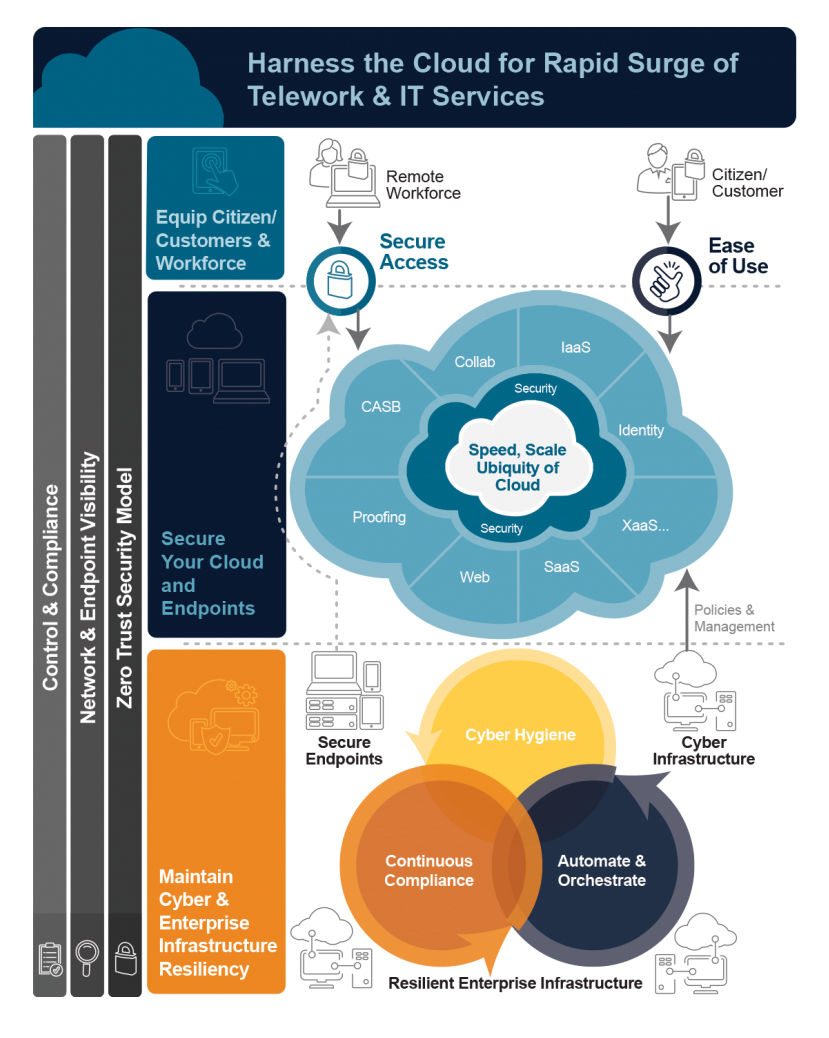
Support remote workers, wherever they may be
A shift in workforce arrangements means that organizations must secure remote workers and anyone else who requires access. That is a challenge as the recent rapid demand for such arrangements has stressed legacy remote access systems, which are not designed to secure remote workers, protect endpoints, or remotely access applications. But by implementing a zero trust architecture, enterprises can adapt to heavily remote workforces, support existing infrastructures, and enhance security all at once.
Merlin helps organizations design secure support for a variety of needs and ensures remote worker identities are properly authenticated. We do this while utilizing current VPNs and existing infrastructure, meaning there’s no need to rip and replace legacy systems. See how we can help your organization secure remote workers with solutions that solve immediate needs today while enabling you to scale and adapt for the future.