CyberArk Helps Agencies Meet Zero Trust Objectives and other Government Mandates
How CyberArk helps federal agencies meet Cyber EO 14028, M-22-09 and other government directives
With a push to implement Zero Trust security across federal government, CyberArk helps agencies achieve their Zero Trust objectives with capabilities centered around securing identities and enforcing least privilege - a key tenet of Zero Trust.
CyberArk and Merlin have partnered to help US federal agencies standardize on CyberArk Privileged Access Management (PAM), a critical capability in Zero Trust security. Government is implementing PAM for human and non-human identities to establish a foundational state of security control in alignment with Zero Trust security principles. PAM can help with:
- Discovery and management of privileged credentials;
- Isolation of credentials and sessions;
- Recording and auditing sessions; and
- Security of credentials for privileged users and applications.
With the latest innovations from CyberArk, a modern Identity Security platform that combines PAM, Access Management, and Identity Management is available to further advance agencies’ Zero Trust journey. Centered on Intelligent Privileged Controls, this Identity Security platform provides seamless and secure access for all identities with flexible identity automation and orchestration.
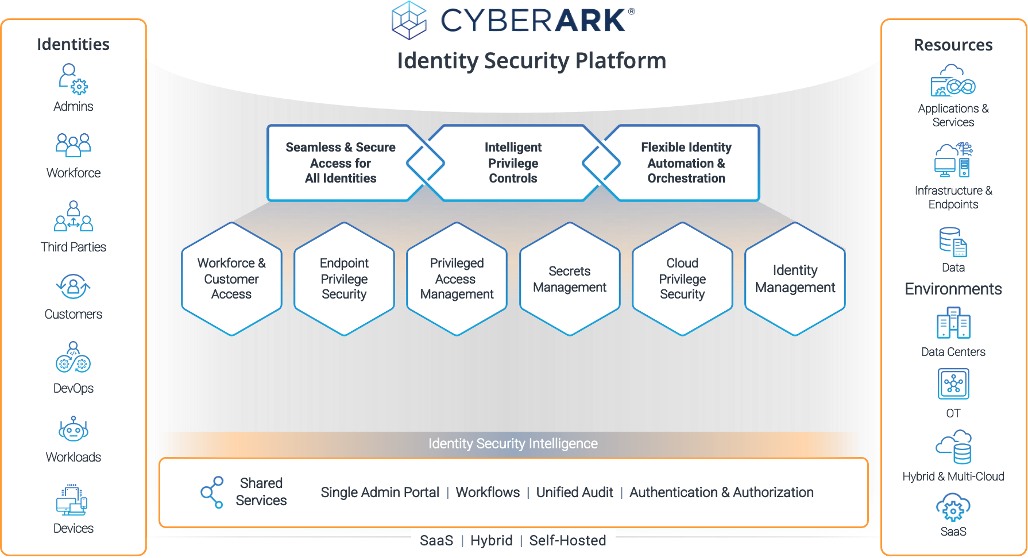
A modern approach to Identity Security centered on privilege to protect against advanced cyber threats
CyberArk’s solutions help US government modernize cybersecurity and advance towards Zero Trust architecture as required in the Cybersecurity Executive Order 14028 and OMB M-22-09. Furthermore, the solutions improve detection and response to identity-based threats with enterprise logging capabilities and advanced security analytics. It is no longer sufficient to simply identify who is on the network; Zero trust principles require agencies to enforce least privilege, to have better detection and response against anomalous behavior, and to uniformly enforce security policies that limit access – both for users and non-person entities.
Recent directives and memoranda (several listed below) further solidify the business case for CyberArk’s solutions. At Merlin, we help our government customers and partners identify the right solutions to meet their mission needs.
Government Directives and Memoranda
| Government Directive / Mandate | Date | Guidance | Solutions | |
|
EO 14028 |
Executive Order on Improving the Nation’s Cybersecurity (EO14028) |
May 2021 |
Modernize Federal Government Cybersecurity: |
|
|
M-21-31 |
Aug 2021 |
Requires agencies to log the creation, use and deletion of identities and credentials. Furthermore, logging for "Monitor, Alert and Respond to Anomalous Behaviors/Activities” |
|
|
|
M-22-09 |
M-22-09 Moving the U.S. Government Toward Zero Trust Cybersecurity Principles |
Jan 2022 |
Requires agencies to achieve Zero Trust security goals by end of FY24, to include: strong MFA, authentication, and centralized ID management |
|
|
M-22-18 |
Sept 2022 |
“…agencies are expected to take appropriate steps to adopt and implement secure software development practices for agency-developed software.” |
CyberArk Secrets Manager |
|
|
BOD-23-01 |
Oct 2022 |
“Vulnerability enumeration performed on managed endpoints (e.g., servers, workstations, desktops, laptops) and managed network devices (e.g., routers, switches, firewalls) must be conducted with privileged credentials.” |
CyberArk Secrets Manager |
|
|
DOD ZT |
Nov 2022 |
DOD ZT User Pillar: continually authenticate, access and monitor user activity patterns to govern users’ access and privileges while protecting and securing all interactions. |
|
|
|
CISA ZT |
April 2023 |
Access Management: Agency uses automation to authorize just-in-time and just-enough access tailored to individual actions and individual resource needs |
|



