Blog Series: Supporting the Secure Workforce — Cyber Resilience
Manage and Secure the Endpoints – Protect the Enterprise
“Down to just essential personnel working onsite, how do I support this rapid surge of remote teleworkers and IT services?”
Surge Readiness of People, Process and Technology
This is a common theme we hear a lot from our customers. Operational efficiency is critical to successfully address this surge. We see this firsthand with the growing adoption and use of cloud services. When enabling the secure remote teleworker, besides the cloud service, there are two other critical control points for policies and management: the endpoint and the enterprise cyber infrastructure. These two critical control points are inherently intertwined where configuration settings, controls, and policies are applied and continuously feed information to each other to adapt and improve overall security posture.
How Secure are Your Endpoints? The Need to Protect Against Peripheral-Based Threats
Threats to our endpoints continues to evolve. Whereas anti-virus/ malware technology used to be adequate for endpoint security, threat actors are using signature-less, file-less or zero-day attacks on our endpoints essentially making traditional anti-virus/malware tools less effective. As a result, endpoint security has evolved to include endpoint detection and response (EDR), and more broadly endpoint protection platforms (EPP). Many of these solutions use machine learning and utilize the cloud for speed, scale and operational efficiencies. We strongly recommend the use of EDR/EPP as a first line of defense for your endpoints. Specifically, for remote teleworkers utilizing a cloud-based EDR solution can improve IT operational efficiencies with easier updates, threat detection and response.
Another threat vector that is emerging are rogue peripheral device attacks. Unlike threats that capitalize on vulnerabilities in the operating system or applications, rogue device attacks operate at the physical layer, beneath traditional detection mechanisms. Often appearing as trusted devices to the operating system (i.e. USB hubs, keyboards, mice, etc.), they can bypass device policies and pose a hidden threat to endpoints. Recently, this BadUSB attack concealed as a fake Best Buy gift card shipped to a hospitality customer contained malware. This threat can be more acute in remote telework scenarios with the vast number of consumer peripherals and lack of IT visibility.
The image below is of a compromised mouse which contains a wireless controller that captures and transmits data to external sites. Supply chain hacks such as these have become more prevalent and agencies need a way to protect against them.

Ensure Productivity with Comprehensive Endpoint Visibility and Control
Real-time visibility, control and compliance of endpoints — especially in remote telework scenarios — is critical for operational effectiveness. A performant, functional and secure endpoint is crucial for agency teleworkers to remain productive and deliver on the agency’s mission. Proactively monitoring, measuring performance and remediating at scale is a critical element of the secure, remote workforce.
Monitor and Maintain Cyber and Enterprise Infrastructure Resiliency
This brings us to the last logical control point of our approach and arguably the most critical component: our agency’s cyber and enterprise infrastructure. IT services, policies, technologies and staff all emanate from our agency’s own premises. This still holds true even as we support a secure remote workforce.
The Principles of Zero Trust
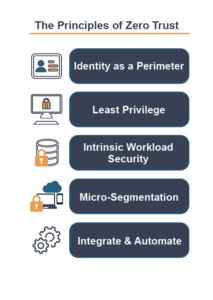
The Interim Telework Guidance speaks well to the need for establishing good cybersecurity hygiene for teleworkers and cyber infrastructure. Specifically, doing standard practices like backup & recovery, vulnerability assessments, auditing and inventory should be standard operating procedures. Merlin has developed a Zero Trust Security model that contains foundational and critical security principles that support a secure remote workforce. These are based on the core tenets of: Identity, Workload and Network Security.
Having comprehensive telemetry and appropriate policy control points to secure the remote workforce is enabled through this zero trust security model.
Adapt, Automate, Detect, Respond
With the expanded threat landscape brought by the remote workforce, it is important to ensure that your cyber defense tools can adapt to the changing environment. Machine learning/AI-based solutions can effectively detect and protect your network against known and unknown threats. Furthermore, it’s important to ensure that your solution can integrate with the control points we discussed, whether they reside in the cloud, endpoints, or infrastructure.
With limited staff and growing demand on IT, orchestration and automation are even more relevant. Turning rudimentary, manual processes into automated workflows saves time for IT. An extensible platform with an open API framework provides quick and seamless integration into enterprise security tools, business systems and corresponding workflows.
At Merlin, we partner with market leaders and innovators in cybersecurity to bring you mission-ready solutions. We have a comprehensive approach to delivering an end-to-end security framework based on zero trust security principles to secure you remote workforce. Reach out to us for a briefing or demo of any of the solution capabilities described in our blog series.



